-
Product Management
Software Testing
Technology Consulting
-
Multi-Vendor Marketplace
Online StoreCreate an online store with unique design and features at minimal cost using our MarketAge solutionCustom MarketplaceGet a unique, scalable, and cost-effective online marketplace with minimum time to marketTelemedicine SoftwareGet a cost-efficient, HIPAA-compliant telemedicine solution tailored to your facility's requirementsChat AppGet a customizable chat solution to connect users across multiple apps and platformsCustom Booking SystemImprove your business operations and expand to new markets with our appointment booking solutionVideo ConferencingAdjust our video conferencing solution for your business needsFor EnterpriseScale, automate, and improve business processes in your enterprise with our custom software solutionsFor StartupsTurn your startup ideas into viable, value-driven, and commercially successful software solutions -
-
- Case Studies
- Blog
Complete HIPAA Compliance Checklist for Your Software Product
The 1996 US Health Insurance Portability and Accountability Act (HIPAA) has become one of the main laws that dictates how medical software must work. Businesses that don’t comply with HIPAA can pay hefty fines. In 2018, the Office for Civil Rights received $28,683,400 in financial penalties from companies and organizations that ignored HIPAA. If you don’t want to be the next company to pay a tremendous fine, keep on reading and get a complete HIPAA compliance checklist for your software product!
Introduction to HIPAA
HIPAA is an act that was created with one major goal ‒ to establish clear rules concerning the gathering, storage, use, transfer, exposure, and destruction of medical data by all sorts of medical establishments and other parties who have access to such data. The clear requirements laid out by HIPAA for working with personal data protect patients and allow them to make informed decisions.
Unlike similar acts, HIPAA is mandatory but has power only on the territory of the US. In case organizations transfer data outside the US, such data is no longer protected by HIPAA.
To make sure your medical software is HIPAA compliant, you need to understand the main terms used in the law and take a look at some key HIPAA rules.
Protected health information
HIPAA is concerned with protected health information (PHI) or electronic protected health information (ePHI). It defines PHI as the following:
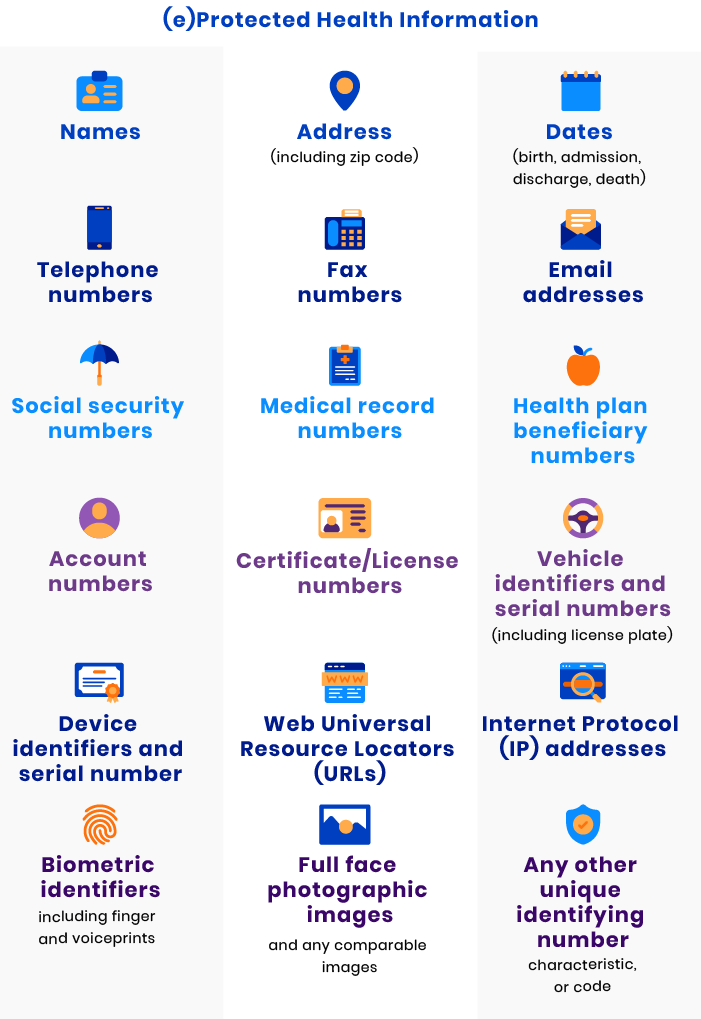
Covered entity
A covered entity is a specialist (like a doctor or a nurse) who works in the healthcare industry and has access to PHI.
Business associate
These are non-medical specialists like IT specialists and lawyers who work with covered entities and can also have access to (e)PHI.
Now it’s time to get acquainted with the HIPAA rules that have the most influence on your software product.
HIPAA Privacy Rule
The Privacy Rule is one of the main rules HIPAA is based on. It creates a national standard for protecting all sorts of medical records and other personal healthcare information.
The goal of the Privacy Rule is to give individuals full control over their private information, improve data security, assign clear responsibility for (e)PHI, and describe the legal process for using and releasing (e)PHI.
HIPAA Security Rule
The Security Rule was added in 2005 to set norms for how covered entities treat personal health information that is produced, saved, transferred, or received in an electronic format.
HIPAA Omnibus Rule
The HIPAA Omnibus Rule was added to expand the definition of business associates to include all third-party contractors, obliging them to comply with HIPAA privacy, security, and breach notification rules while dealing with PHI.
There are a lot of other rules in HIPAA that affect your company’s workflow, physical protection of workspaces, internal network, and violation policy. However, in this post, we’ll discuss only HIPAA requirements for software protection and provide a checklist to test your software product. So what does it take to become HIPAA compliant? Let’s get this sorted out!
HIPAA compliance checklist for your software product
HIPAA requires you to use the most reliable technologies to secure your software and all the data it works with. However, HIPAA doesn’t name precise technologies or tools. The authors of the law intentionally decided not to narrow your choice to technologies that will become outdated in a year or two. That means you’re free to pick the technology stack, toolset, and security features for your project.
Nevertheless, HIPAA has a list of requirements any healthcare software has to meet. We’ve created a clear checklist of the steps you need to take to make your healthcare app HIPAA compliant.

#1 Strictly control access
Your software product may process tons of ePHI. However, not all employees need the same access to this data to do their jobs. By setting up role-based access control in your software, you can limit access to only the data employees really need. Thus, you can protect data not only from malicious intent on the part of your employees but also from human errors.
Pro tip: To implement role-based access control in your software, you can start with defining all specialists who will be working with your product. These are not only doctors and nurses. Think about administrators and technical staff too.
Once you’ve defined all users of your software, make a list of the types of data these specialists will need to access to perform their work. It’s better to limit workers’ access to a minimum of data than to give access to data you think they might need. If specialists require information they don’t have access to, they can request it when necessary.
#2 Limit session times
To enhance the security of PHI, you can limit session times. This means users will be automatically logged out after some period of time if they don’t do anything in the system. This way, you can protect your software and information by preventing unauthorized users from accessing information if a device has been left unsupervised.
Pro tip: You don’t necessarily have to make the session time the same for all users. Some users can have longer sessions if their work requires it.
#3 Encrypt data
It may seem confusing that HIPAA defines PHI encryption as an optional step. The thing is that it’s up to you whether to encrypt your data. The only thing that matters for HIPAA is data security. That means you can choose another approach to protect data — like tokenization, for example.
Nevertheless, data encryption is a comparatively easy and fast way to protect medical information.
Pro tip: If you choose encryption over any other security approach, make sure you use only the most reliable encryption protocols, like those that meet the demands of the National Institute of Standards and Technology. And one more thing: even the most reliable encryption is worthless if you store the keys in an accessible place.
#4 Implement an activity tracking system
Your software system can track users’ activities and identify patterns based on regular actions. Thus, the system can detect suspicious actions and alert you about them. As a result, you can get additional time to prevent a data breach and data theft.
Pro tip: A tracking system helps you not only prevent a breach but investigate an incident that’s already happened. By recording all actions and IDs of workers, you can easily find out who was the last to work with the system or how hackers got inside.
#5 Back up data
Backing up data and securely storing it is compulsory for all parties who have access to PHI. The law demands a copy of all data be stored on a reliable third-party server separate from the original data. This third-party server is necessary to restore the information in case of data losses.
Pro tip: Make sure you back up your data frequently. It will give you the confidence that even data you’ve added recently is securely stored and can be recovered if needed.
#6 Ensure secure authentication
There are a lot of approaches you can take to ensuring secure authentication. HIPAA doesn’t limit you, so you can choose the most reliable approach at your discretion.
Pro tip: If we look at software products that require the highest level of security (banking apps, for instance), we can see that these are the most popular authentication solutions nowadays:
- Multi-factor authentication. This is a reliable authentication approach that requires users to enter a login and password along with an additional parameter that represents a different factor of authentication, like a one-time password.
- Biometrics. You can employ biometric authentication if your employees work on mobile devices, tablets, or laptops with special sensors that can scan a fingerprint or recognize a face.
- Expiring passwords. It goes without saying that all users of your product must have strong passwords. However, you should also remember that passwords that are updated frequently can secure your software from an angry ex-employee or hackers who may steal passwords.
- Risk-based authentication. Risk-based authentication is a complex procedure that involves calculating a risk score each time someone attempts to enter the system. A risk-based authentication solution tracks the number of access attempts, used devices, IP addresses, geolocation, and other parameters. In case the system sees a discrepancy, it asks a user to pass an additional verification procedure.
- Physical means of identification. These can be either physical cards or electronic keys or tokens stored on physical memory cards that users need to activate with a password. Such keys or tokens cannot be copied or hacked.
#7 Ensure secure data transfer and storage
Another puzzle you need to solve is where to store data and how to transfer data securely to that location. Physical servers are expensive and difficult to protect. That’s why cloud storage is the best option.
Pro tip: Choose a cloud service provider like Dropbox or Google Drive that’s HIPAA compliant out of the box.
#8 Protect correspondence
While HIPAA doesn’t require companies to encrypt their email correspondence, the necessity to encrypt emails becomes clear when you dive deeper into all the HIPAA prescriptions concerning secure PHI transfer. While emails sent within your internal network can go without encryption, all external correspondence should be encrypted with the most secure encryption protocols like AES, OpenPGP, or S/MIME.
Pro tip: If your business model involves frequent correspondence between covered entities (like doctors) and patients, consider implementing a secure chat feature in your software product.
Wrapping up
It may seem that HIPAA’s list of requirements concerning software security is too long. Nevertheless, modern software products from different industries use almost the same approaches we’ve mentioned to protect themselves from hacker attacks and data breaches.
FAQ
-
- Establish strict access controls
- Limit session times
- Encrypt data
- Implement an activity tracking system
- Back up your data
- Ensure secure authentication
- Provide secure data transfer and storage
- Protect correspondence
-
All healthcare software that operates on the territory of the US has to be HIPAA compliant. That’s why you need to use approaches that provide the highest level of security:
- Multi-factor authentication
- Biometrics
- Expiring passwords
- Risk-based authentication
- Physical means of identification
-
To make sure your healthcare software is HIPAA compliant, contact a reliable and experienced quality assurance team that can not only thoroughly inspect your product but also perform security checks to detect and fix all vulnerabilities.










